Microsoft Azure’s Layer 7 load balancing solutions
Exposing applications on the Internet is always a complex matter. Usually, it requires some planning to be able to expose in a secure manner.
One of those aspects includes questions related to web application and the associated security layer which is the Web Application Firewall (WAF).
In this article we will talk about Microsoft Azure’s Layer 7 load balancing solutions, i.e., Application Gateway and Front Door.
We’ll start with a reminder on basics concepts around load balancing and WAF before diving a little deeper into the Azure WAF options.
Load balancing
To start it’s important to understand what load balancing means.
Load balancing is the distribution of workloads across multiple computer resources. It optimizes resource utilization and maximizes throughput, minimizing response time and avoiding overloading of a single resource.
Azure offers Layer 4 and Layer 7 load balancing services.
- Layer 4 works at the 4th layer of the OSI model, the transport layer. The routing decisions are made based on network information (ports, Ips, protocol).
- Layer 7 works at the 7th layer of the OSI model, the application layer. It has access to more information than the 4-layer load balancer like the content of the data packets: URL, header message content, etc. Layer-7 load balancers enhance your application security.
Web Application Firewall (WAF)
Azure Web Application Firewall is a Cloud-native service that operates at level 7 to protect your web applications from bot attacks and common web vulnerabilities such as SQL injection and cross-site scripting.
It provides centralized protection of your web applications from common exploits and vulnerabilities.
A web Application Firewall (WAF) defends your web services against common exploits and vulnerabilities. It keeps your service highly available for your users and helps you meet compliance requirements.
In Azure, WAF can be configured in two modes:
- Detection mode: In this case the firewall is monitoring traffic. Violations and threat alerts are logged however requests are not blocked.
- Prevention mode: The WAF blocks unauthorized requests and intrusions. It also logs the attacks and requests.
Application Gateway
Application Gateway (AG) is an Azure Layer 7 load balancing solution. It provides application delivery controller as a service, offering various Layer 7 load-balancing capabilities.
Application Gateway is integrated to Azure Virtual Network and is deployed in a dedicated subnet. This allows the use of Network Security Groups (NSG). NSGs are a great way to filter your traffic thanks to its inbound and outbound security rules. This restricts access to your backend resources.
Microsoft recommends a /24 subnet for Application Gateway so there’s room for autoscaling and maintenance upgrades.
The service is highly available, scalable, and fully managed by Azure.
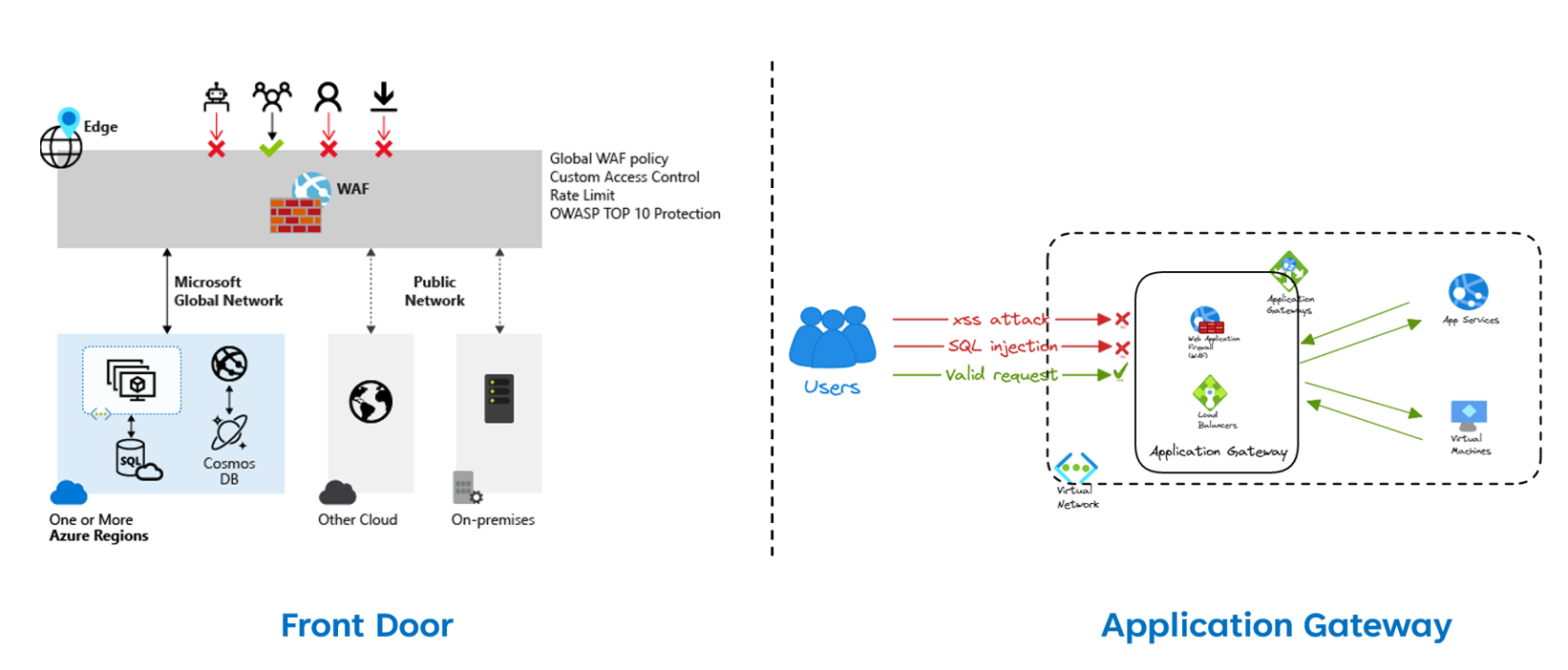
Front Door
Front door is Microsoft’s secure Cloud CDN (Content Delivery Network) service offering various Layer 7 load balancing capabilities. It accelerates delivery while providing reliable and secure access to applications and APIs. It provides dynamic site acceleration with global load balancing features.
Standard and Premium Azure Front Doors combine the capabilities of Azure Front Door (classic), Microsoft CDN (classic), and Web Application Firewall (WAF).
The following features are only supported with Front Door premium:
- Microsoft managed rule set only supported with premium Front Door.
- Bot protection.
- Private link connection to origin.
More details about the differences between the premium and standard tiers here.
Front Door vs Application Gateway
While Front Door (FD) and Application Gateway (AG) are both Azure layer-7 load balancing solutions, there are some differences between the two services.
Global vs Regional
The main difference between AG and FD is that the Front Door is a global service while the Application Gateway is a regional resource.
This means that in case of a regional outage, the Front Door will automatically and easily failover to a different region. While Application Gateway needs to be deployed in different regions with a traffic manager for high availability.
WAF application level
The Front Door applies the WAF at the edge level before traffic gets to your network while the Application Gateway applies the filter at the VNet (Virtual Network) level.
Policy action types
Azure Application Gateway supports the following actions:
- Allow: The request is allowed by the WAF and forwarded to its destination.
- Block: The request is blocked by the WAF.
- Log: The request is logged in the WAF logs. No action is taken.
The Front Door also supports these three plus an additional Redirect action type. With the redirect action the WAF redirects the request to the specified URL.

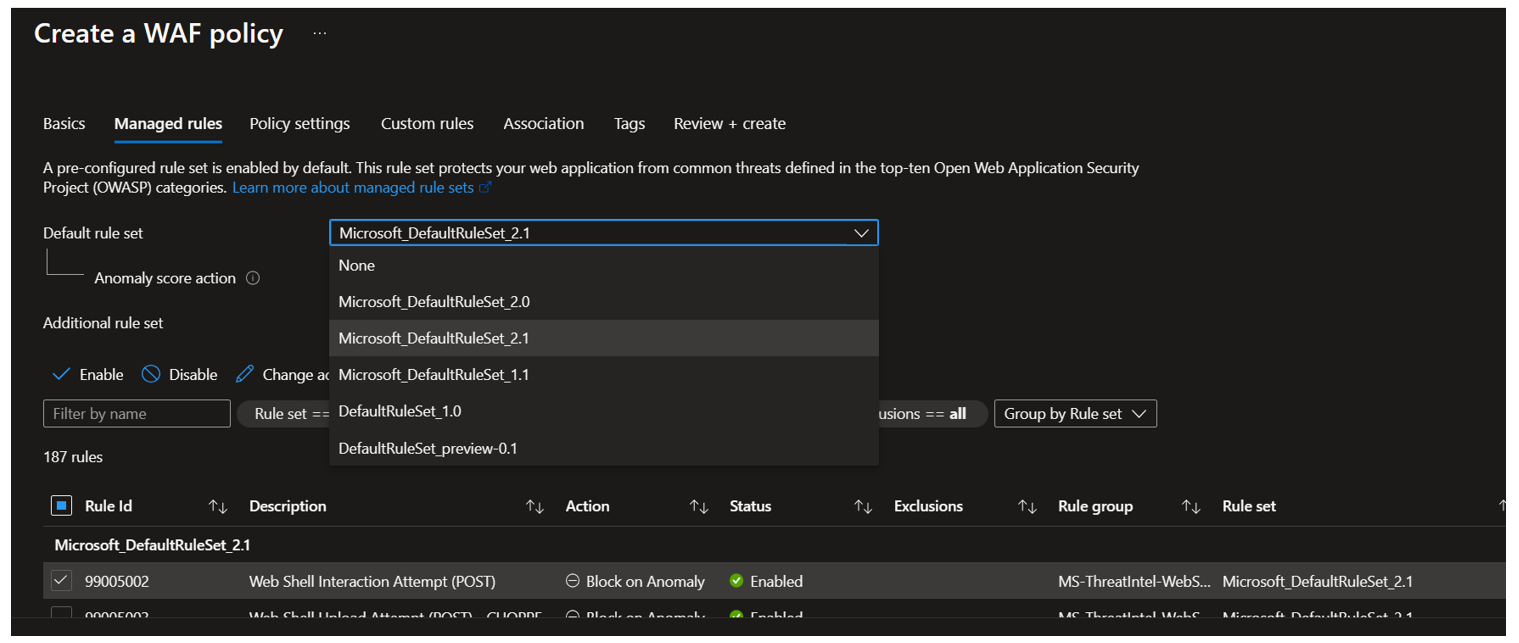
Managed Rules Representation
Application Gateway uses the following representation for its managed rules: OWASP_<version>
Example: OWASP_3.2

Front Door on the other hand, uses the following format: Microsoft_DefaultRuleSet_<version>
Example: Microsoft_DefaultRuleSet_2.1
Custom Rule Types
The Front Door offers two types of custom rules.
- Matching: controls access based on matching conditions
- Rate-limiting: controls access based on the rates of incoming requests.
A rate-limiting rule controls the number of requests from a particular source to an application during a defined period. It helps protect your applications from DDoS attacks.
App Gateway only supports matching rule type.
WAF policy association
For Application Gateway, the WAF policy can be associated with the AG global resource, with a listener or with a path.
With a global policy the configuration to all the applications behind the Application Gateway.
A per-site policy is applied to an HTTP listener and allows you to apply specific settings to each site you have.
The per-URL policy, however, is a path-based rule that lets you customize your WAF settings to the URL level.
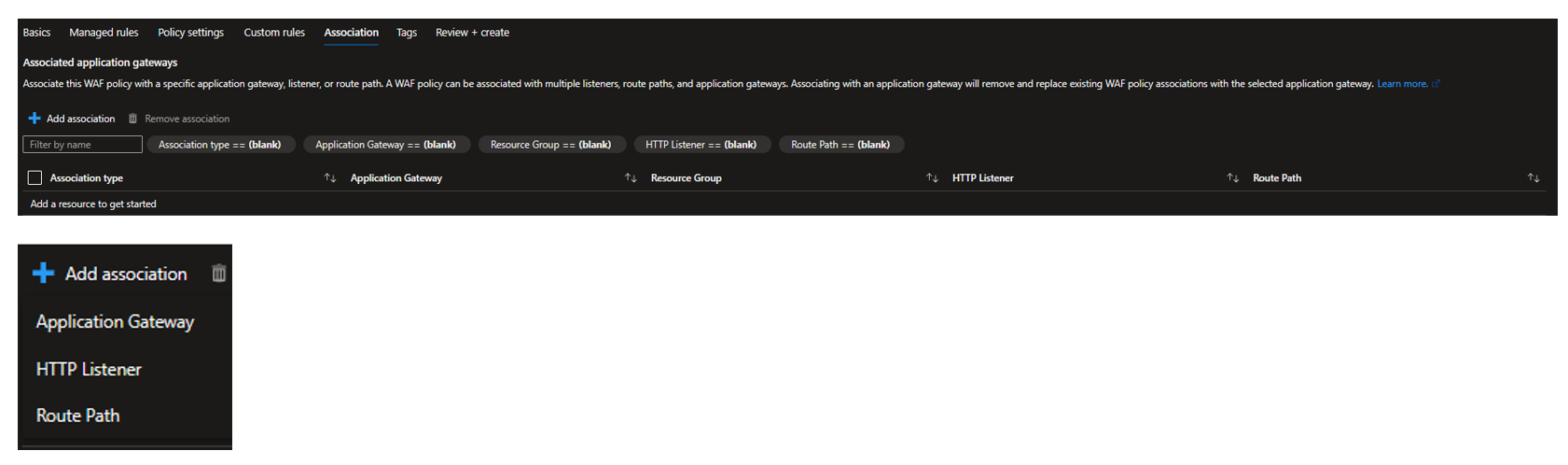
Front Door policy could only be associated to a Front Door profile. Multiple domains can be associated with the profile.

Cost
Cost for Front Door
For Front Door, the cost includes four parts:
- Base Fees (i.e., fixed charge calculated on hourly basis)
- Outbound Data Transfer from Edge to the Client
- Outbound Data Transfer from Edge to the Origin
- Requests incoming from client to Front Door’s edge location.
The data transfer from an origin in Azure data center to Front Door’s edge location is free.
Based on the Front Door SKU the base fees are as follow:

Cost for Application Gateway
Application Gateway cost comprise base fees, capacity units’ fees and outbound data transfers.
Data transfers costs for AG are the following:
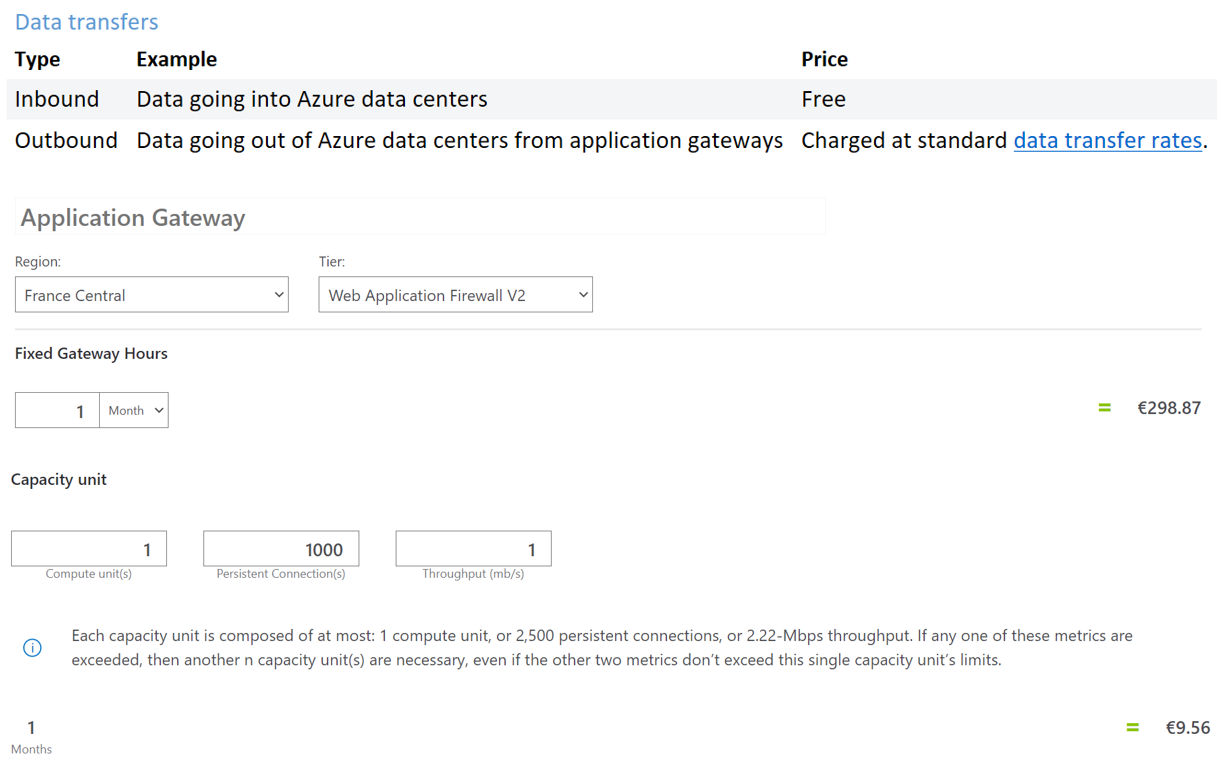
For more details about pricing and tariffication:
- https://azure.microsoft.com/en-us/pricing/details/frontdoor
- https://azure.microsoft.com/en-us/pricing/details/application-gateway/
WAF config
Front Door uses WAF policies to configure its web application firewall.
A WAF policy is an independent Azure resource that contains all the WAF configurations like rules (managed and custom), exclusion, etc.
Application Gateway also supports WAF policies, which is the recommended way to configure your WAF. However, it’s also possible to use the WAF config setting of the AG resource. It’s worth mentioning that it is no longer possible to create an AG from the portal without an associated WAF policy.

When to use Application Gateway behind Front Door?
Microsoft has identified the following scenarios where it could be useful to use an Application Gateway behind Front Door:
- Front Door can perform path-based load balancing only at the global level but if one wants to load balance traffic even further within their virtual network (VNET) then they should use Application Gateway.
- Since the Front Door does not work at a VM/container level, it cannot do Connection Draining. However, Application Gateway allows you to do Connection Draining.
- With an Application Gateway behind the Front Door, one can achieve 100% TLS/SSL offload and route only HTTP requests within their virtual network (VNET).
- Front Door and Application Gateway both support session affinity. While Front Door can direct subsequent traffic from a user session to the same cluster or backend in a given region, Application Gateway can direct affinitize the traffic to the same server within the cluster.
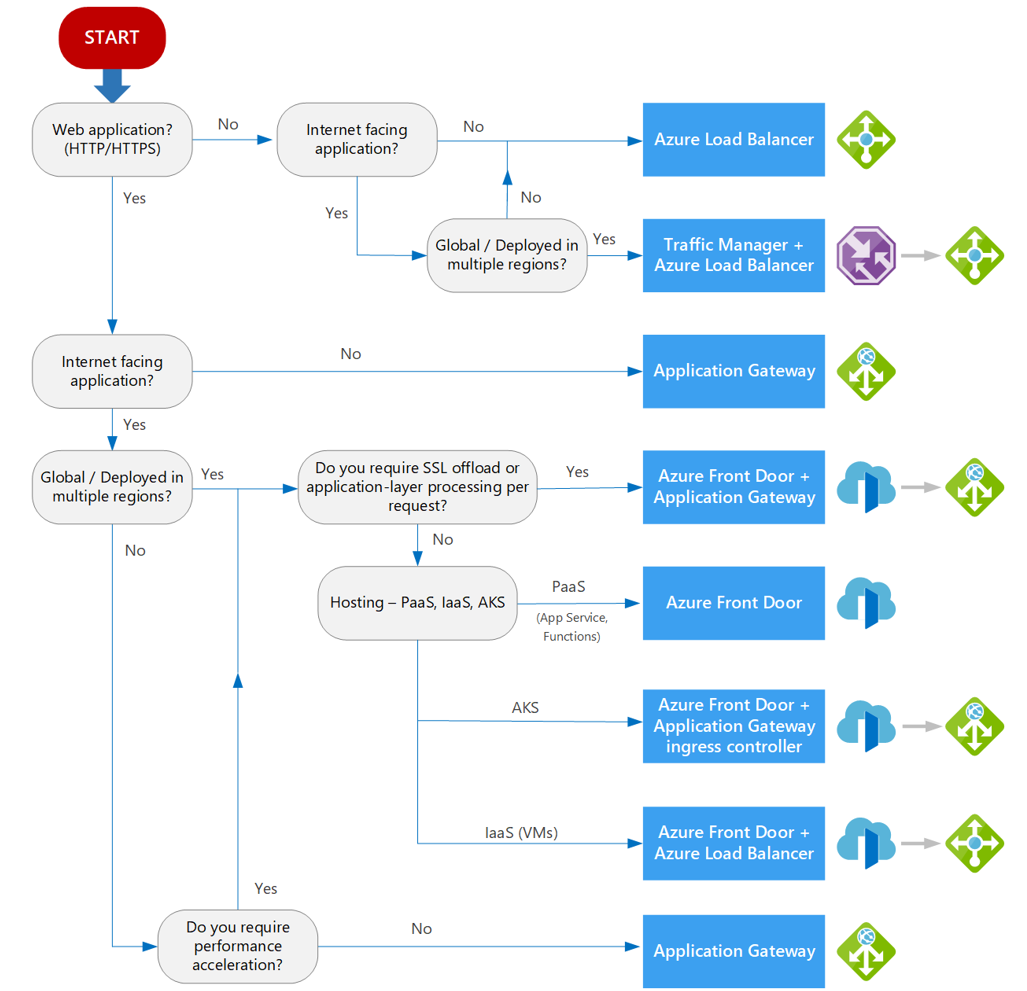
Microsoft Load-balancing Decision Tree
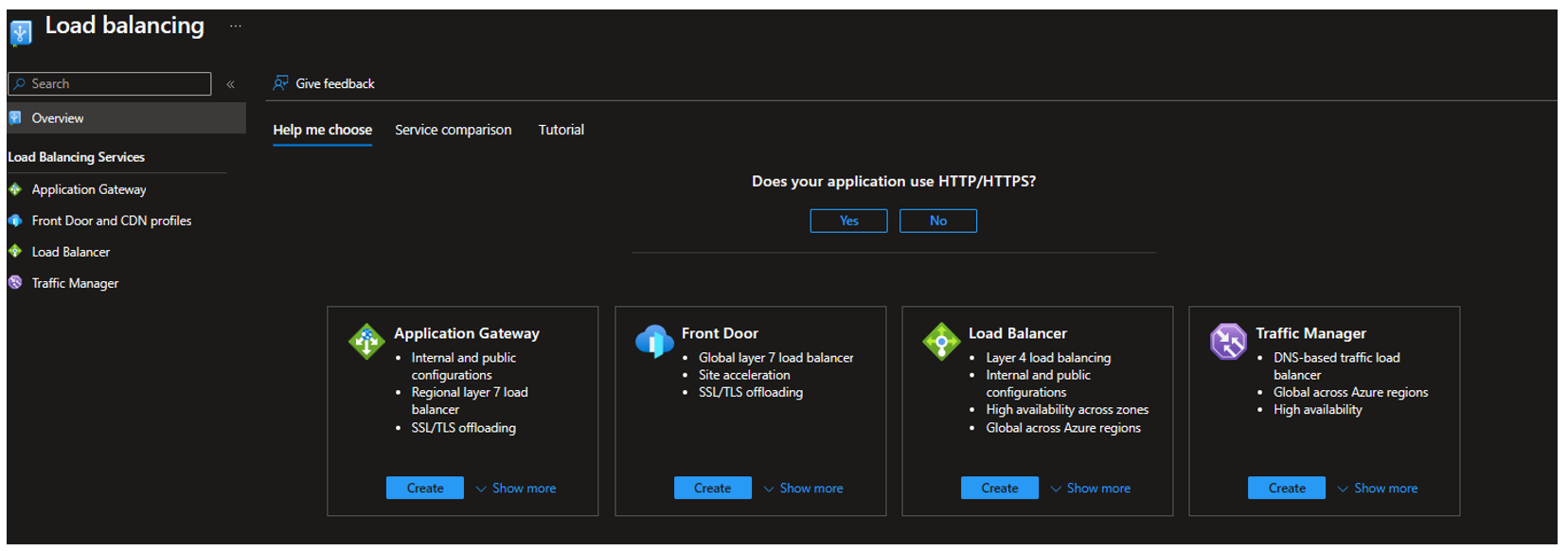
To conclude, Microsoft offers its users a useful decision tree to help them choose the right service for their needs.
The Azure portal can also be helpful deciding which resource to use with the load balancing – help me choose service.
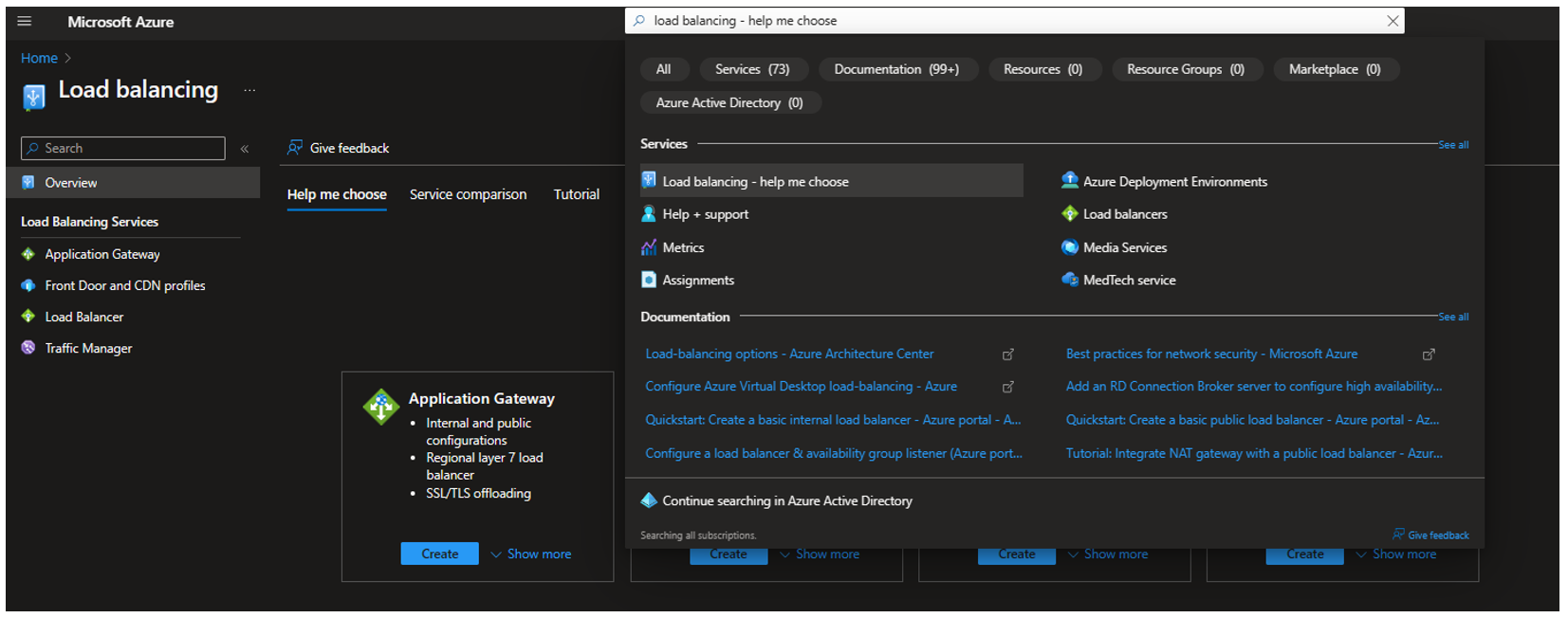
It will ask you a set of questions to determine the right solution for you.
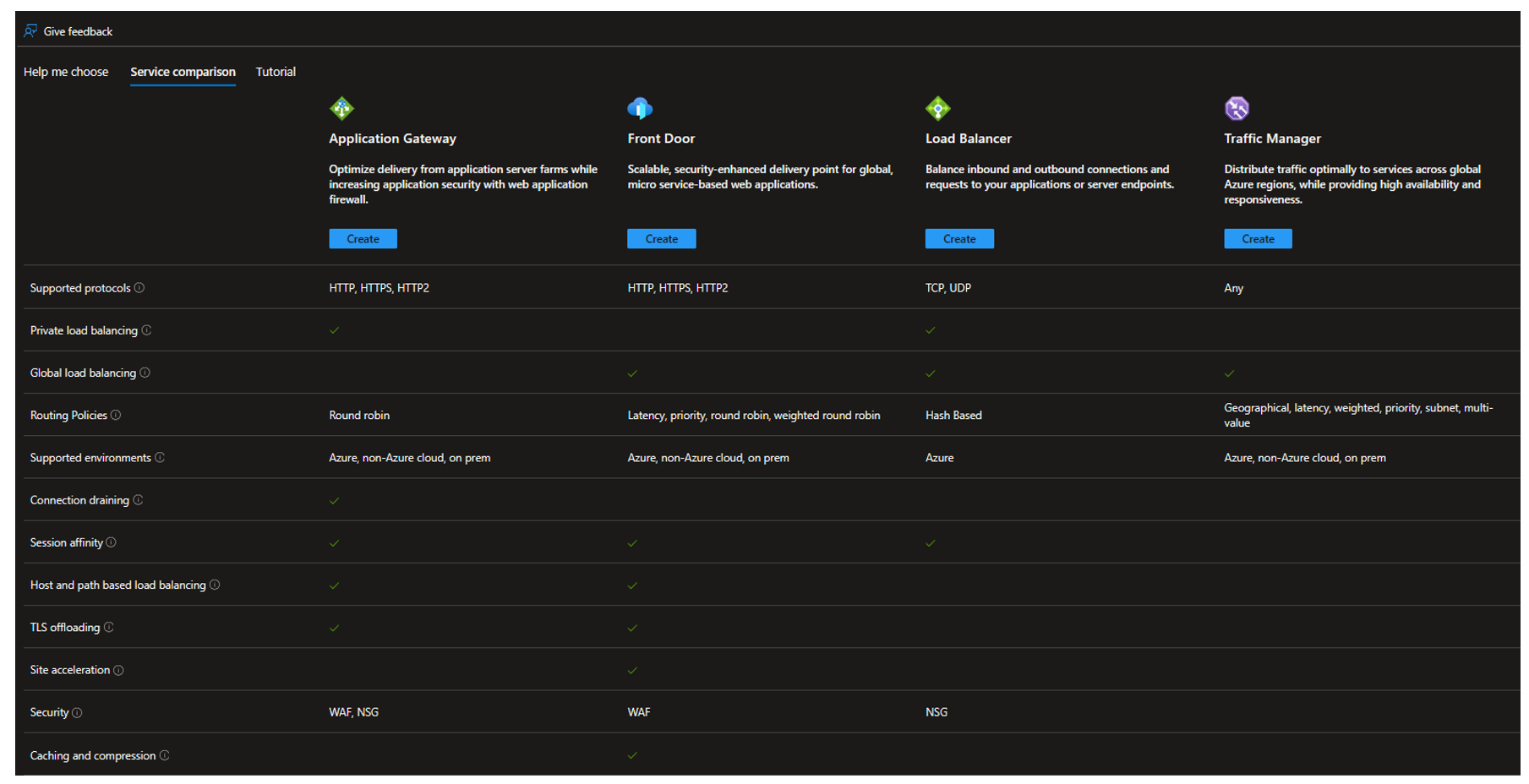
It also has a service comparison tab as follow:
Summary
In this article we talked about the basics of the Azure layer-7 load balancing solutions with a focus on the differences between Application Gateway and Front Door. Hopefully, it will help you understand the concepts and choose wisely for your projects.
The implementation and automation of these solutions with Terraform will be the subject of our next article.